This post spoils a CTF challenge … Don’t read if you want to try it !
Sogeti CTF was a qualifier for the Sogeti Cyber E-Scape. I could not find a team to participate in this event, so I played alone and finally managed to find a team for the final :)
[+] Presentation
La ShadowLeague vous met gracieusement à disposition un gestionnaire de notes. Not bad, huh ?
http://quals.shadow-league.org:8001
**Aucun bruteforce n’est autorisé sur cette épreuve**
[+] Recon
We are facing a simple website with a login form.
We don’t have an account, so let’s register with test:test.
We can now access the web application. It only contains one page, with the possibility to add and view our notes.

It appears that I’m not the first one to use the test account and people already tried many payloads :D
[+] Exploitation
After some fuzzing, the differents forms don’t appear to be vulnerable to XSS neither first order SQL injection …
But, a second order SQL injection is present in this web application : the SQL request which collects the notes for an account uses the username without sanitizing it, so if you register an account with a malicious username, you can exploit this SQL injection to read arbitrary values in the database.
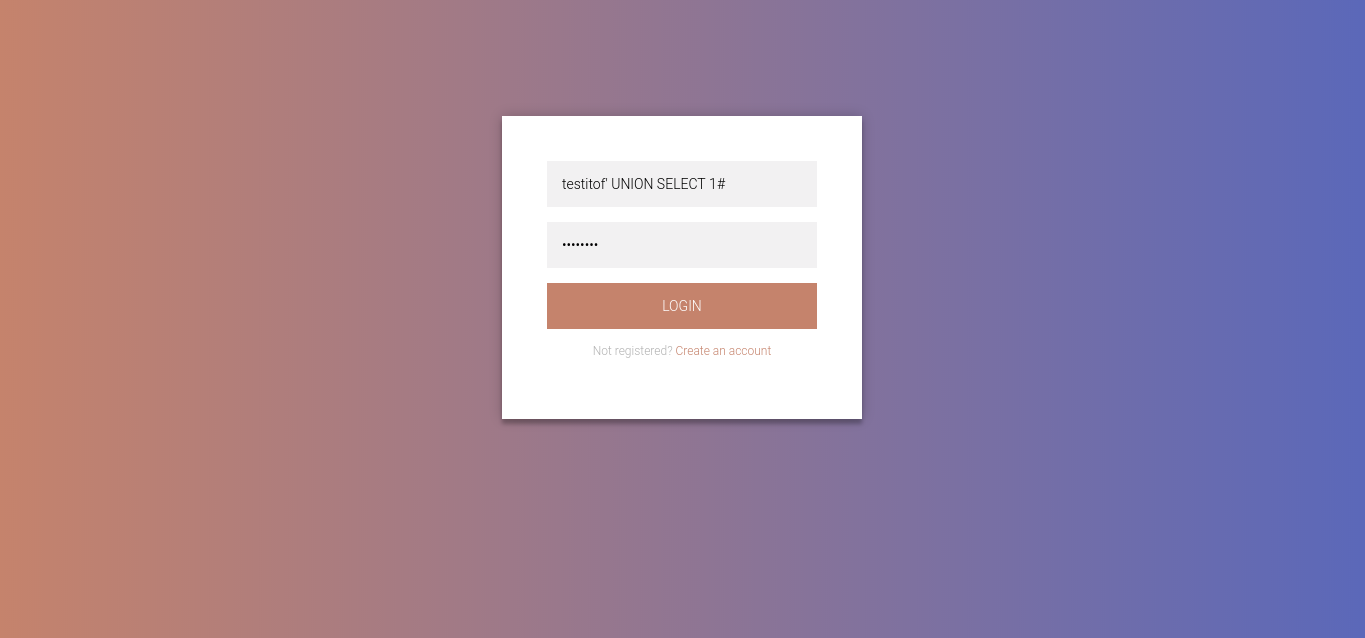
Malicious username = testitof' UNION SELECT 1 #
When you connect to this account, you can see the following note list :
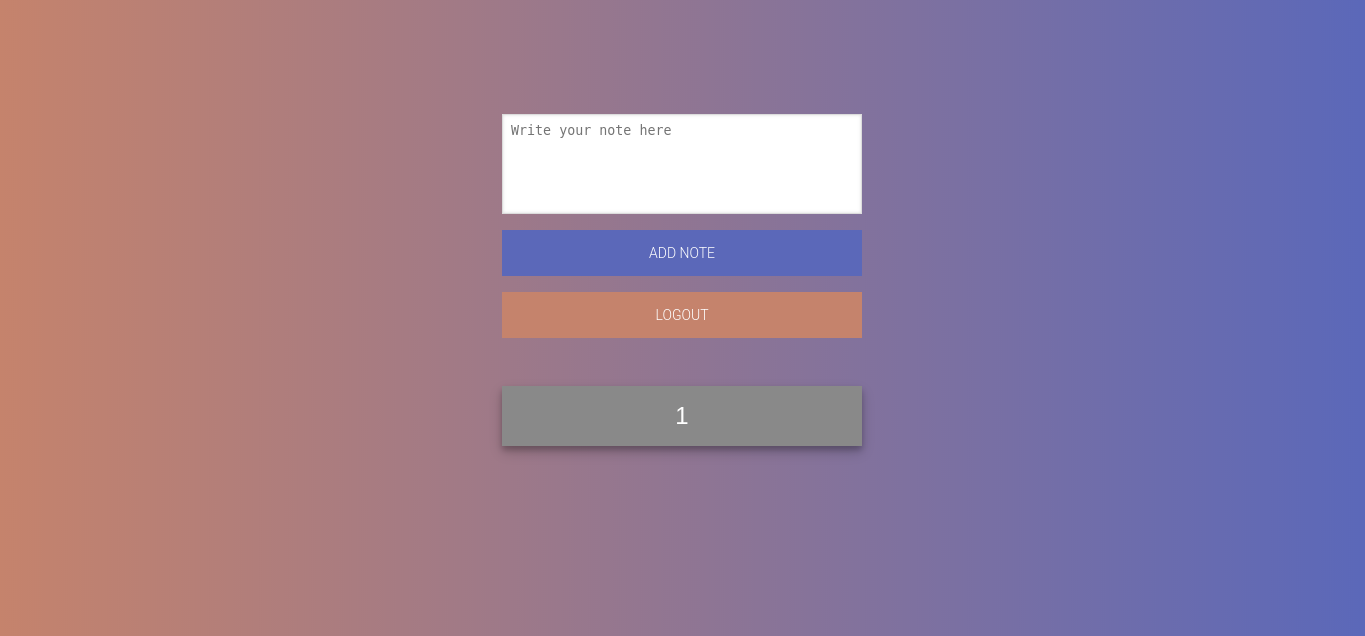
Our payload works, we just have to extract the flag now. After some tests, it appears that the flag is the admin password.
Let’s retrieve it !
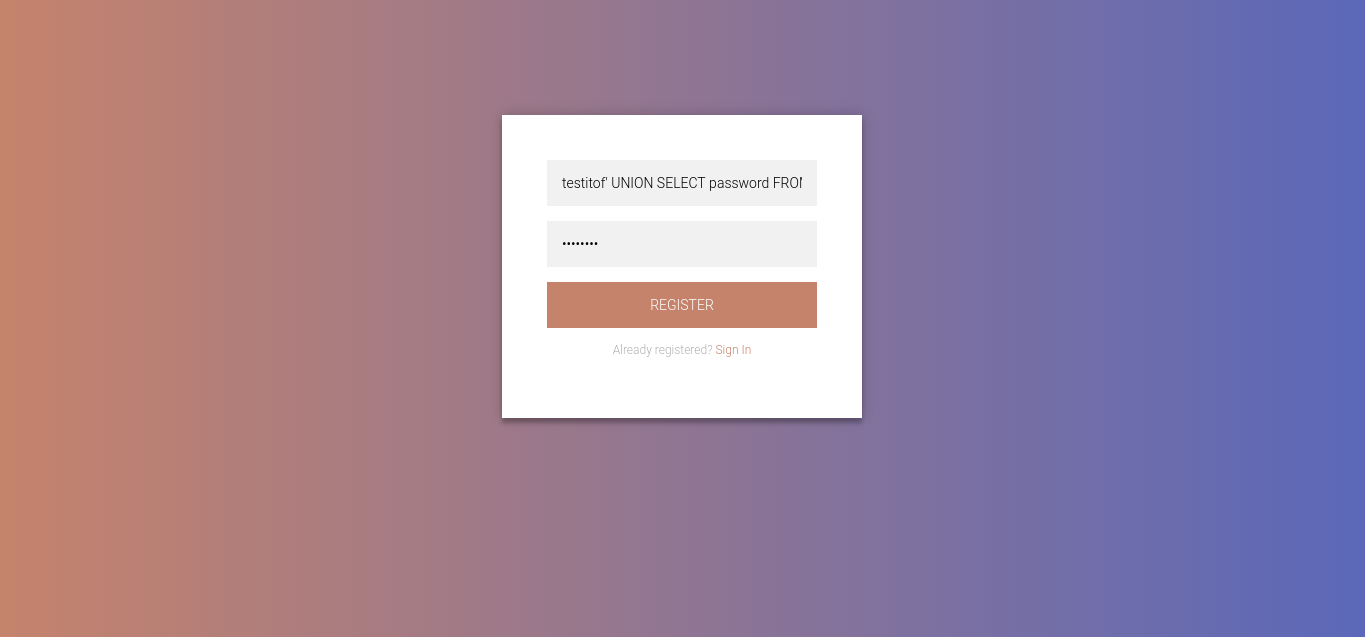
Malicious username = testitof' UNION SELECT password FROM user #
And finally :
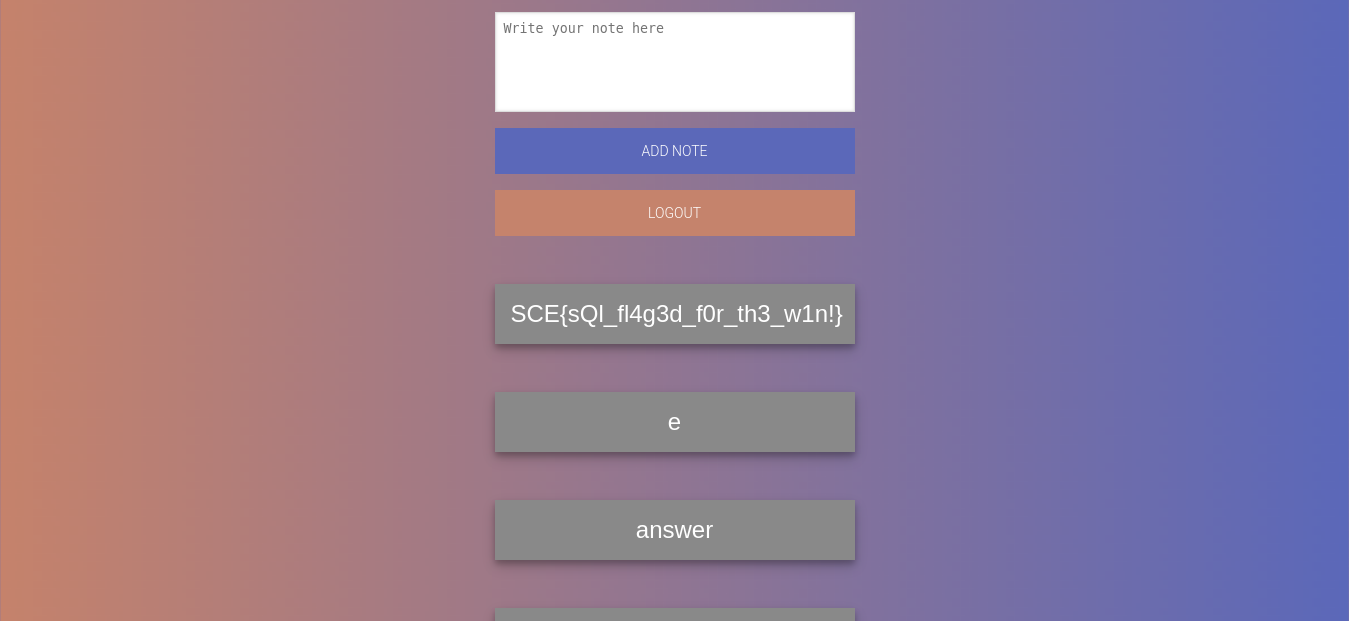
Flag : SCE{sQl_fl4g3d_f0r_th3_w1n!}
[+] Bye
Feel free to tell me what you think about this post :)