This post spoils a CTF challenge … Don’t read if you want to try it !
SantHackLaus is a Jeopardy CTF challenge. It is organized by IMT Lille Douai. I had a great time solving these challenges :D
Mission Impossible 1 is a forensic challenge. We need to recover the flag that has been deleted from the machine by the attacker.
[+] Recon
We just have two file : challenge.elf and his checksum challenge.md5.
The file challenge.elf is a Linux memory dump. Let’s analyze it with Volatility.
I didn’t have a profile for this Linux version (Debian8-3_16_0-amd64x64), so I created one with the following tutorial.
First, let’s enumerate the processes in this memory dump with pstree.
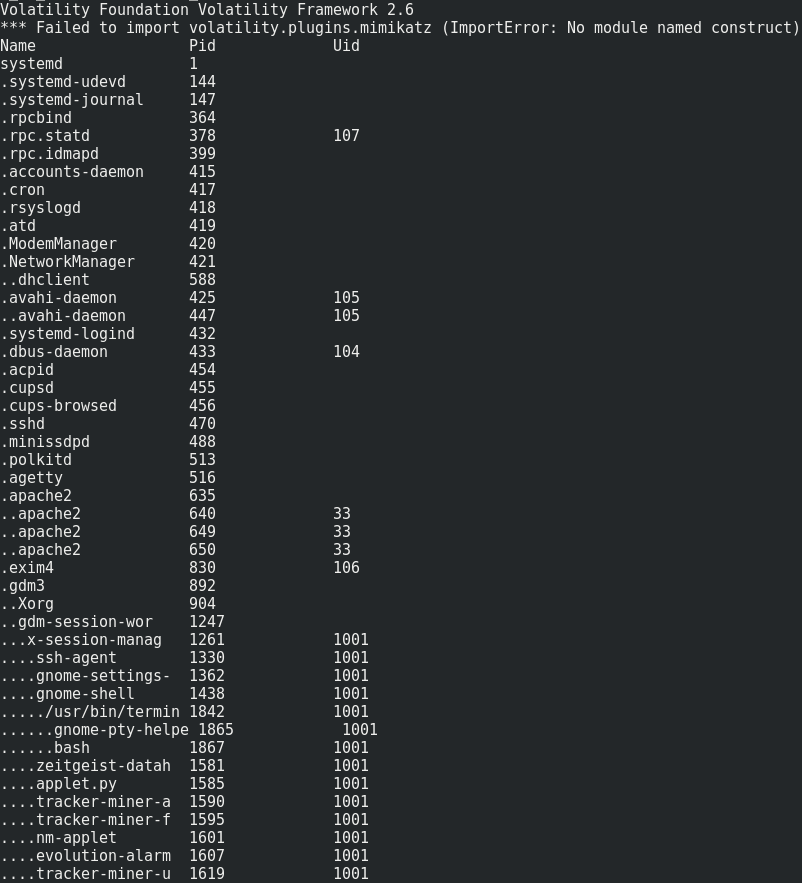
volatility --plugins='volatility_plugins/' -f challenge.elf --profile=Linuxdebian8-3_16_0-amd64x64 linux_pstree
We mainly notice that bash and an apache server are running. Let’s look if there is something interesting in bash history.
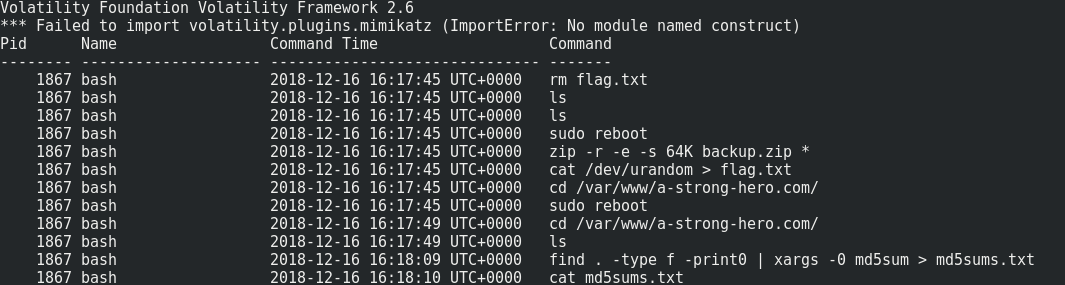
volatility --plugins='volatility_plugins/' -f challenge.elf --profile=Linuxdebian8-3_16_0-amd64x64 linux_bash
Sounds great ! The attacker’s working directory was /var/www/a-strong-hero.com/. Let’s try to enumerate files in this directory.
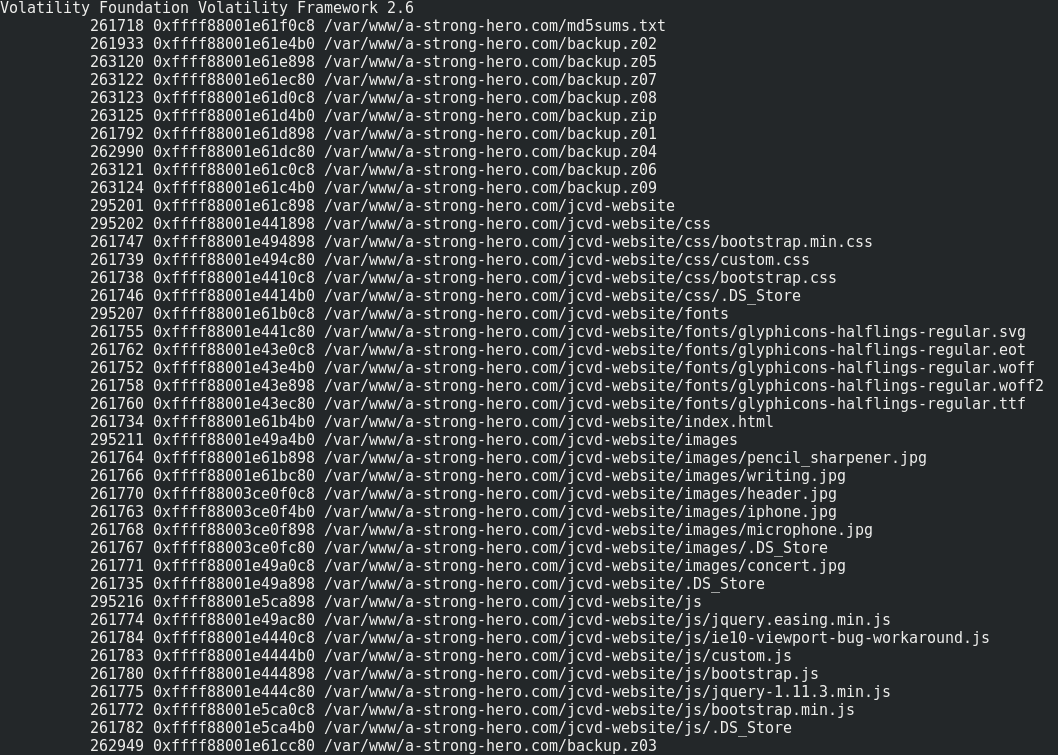
volatility --plugins='./volatility_plugins/' -f challenge.elf --profile=Linuxdebian8-3_16_0-amd64x64 linux_find_file -L |grep '/var/www/a-strong-hero.com/'
[+] Recovery
There are some interesting files. We can mainly notice a backup.zip multipart archive.
Let’s retrieve the archive with the following command for each part :
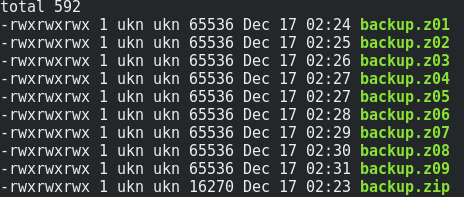
volatility --plugins='./volatility_plugins/' -f challenge.elf --profile=Linuxdebian8-3_16_0-amd64x64 linux_find_file -i 0xffff88001e61d4b0 -O backup.zip
We now have all archive parts. We now need to combine them in one archive with the following command : zip -s 0 backup.zip --out backup2.zip
The resulting archive is password-protected… It’s only possible to enumerate the files it contains with “strings”.
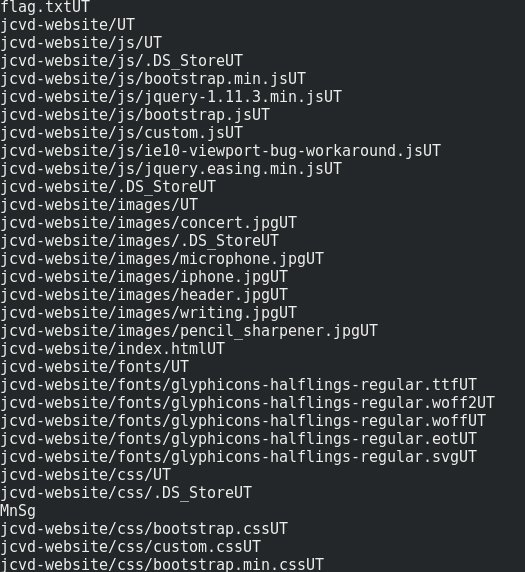
strings backup2.zip
We can notice that some of these files are available in plaintext in the memory dump. We can then use the known plaintext attack on this zip file with pkcrack to recover it.
I will use the bootstrap.js file.
Let’s first recover this known file from memory volatility --plugins='./volatility_plugins/' -f challenge.elf --profile=Linuxdebian8-3_16_0-amd64x64 linux_find_file -i 0xffff88001e444898 -O bootstrap.js and zip it zip boots.zip bootstrap.js.
We can now run pkcrack to recover the encrypted archive, and read the flag inside : pkcrack -c "jcvd-website/js/bootstrap.js" -p "bootstrap.js" -C backup2.zip -P boots.zip -d decrypted.zip -a.
Flag is : IMTLD{z1p_1s_n0t_alw4y5_s4fe}.
[+] Bye
Feel free to tell me what you think about this post :)