This post spoils a CTF challenge … Don’t read if you want to try it !
Sogeti CTF was a qualifier for the Sogeti Cyber E-Scape. I could not find a team to participate in this event, so I played alone and finally managed to find a team for the final :)
[+] Presentation
We are given an .iso file (USB.iso), which is the USB stick dump in which the flag is hidden.
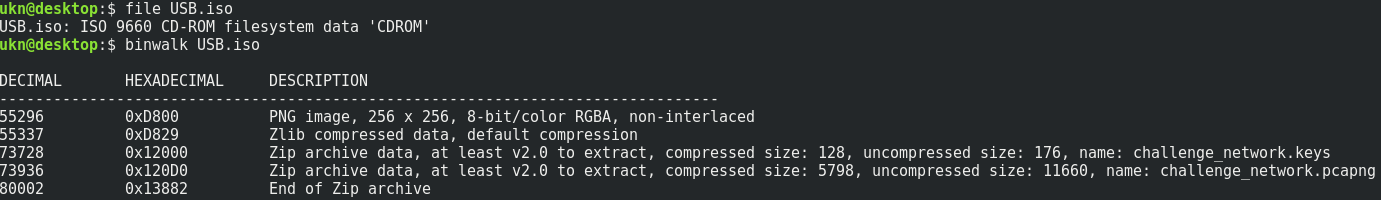
Let’s mount and explore it.
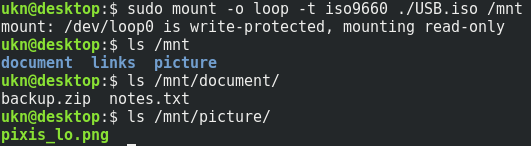
.PNG and notes.txt files are not important here, but let’s dig into backup.zip.
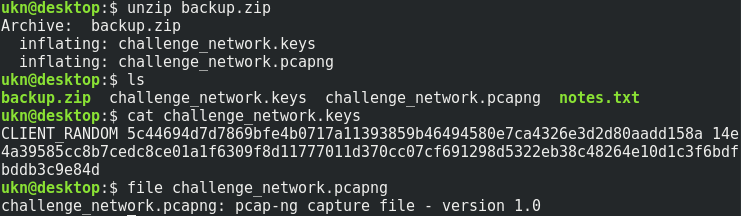
challenge_network.pcapng is a network capture, and challenge_network.keys contains keys usually used to decrypt HTTPS traffic.
Let’s analyse this network capture with Wireshark.
[+] Network analysis
After filtering ARP pollution, we can see that this capture is mainly with TLS (probably HTTPS) and IRC (a chat protocol) traffic.
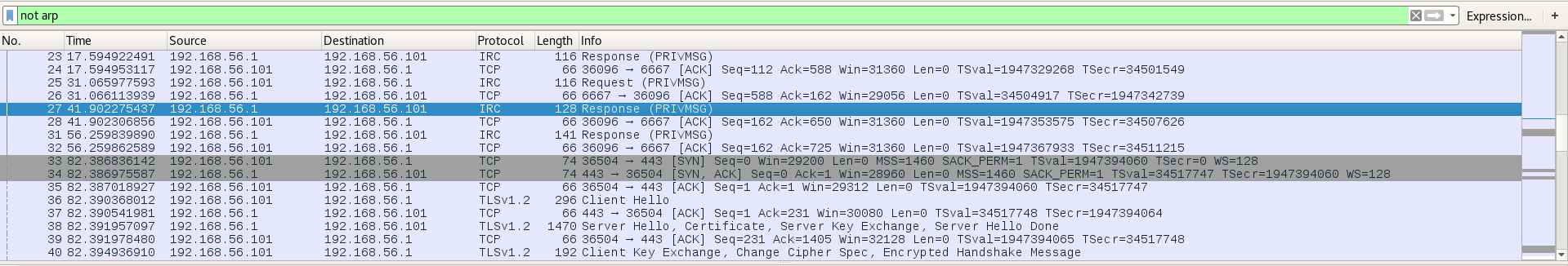
As the IRC traffic is not encrypted, let’s analyse it first.
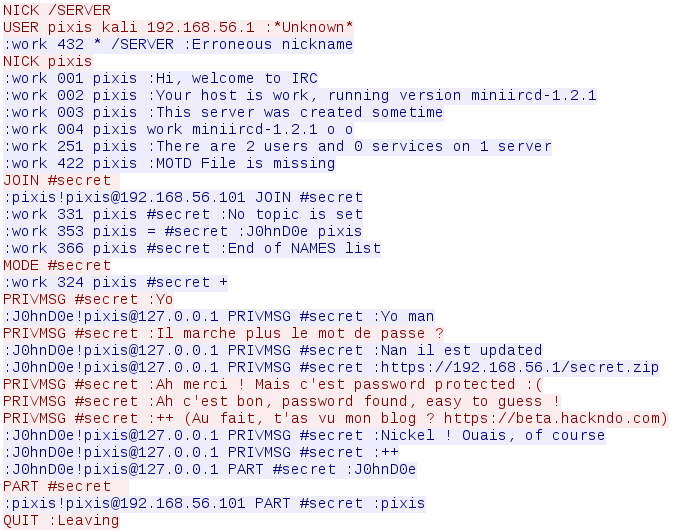
Right click > Follow TCP stream
By reading the chat (french baguette only), we can understand that the https://192.168.56.1/secret.zip contains the flag. This archive is password protected and not directly accessible, but one of the IRC users downloaded it, and said that the archive password is ‘easy to guess’.
With the help of the previously discovered keys, we can decrypt the TLS traffic and find the secret.zip archive.
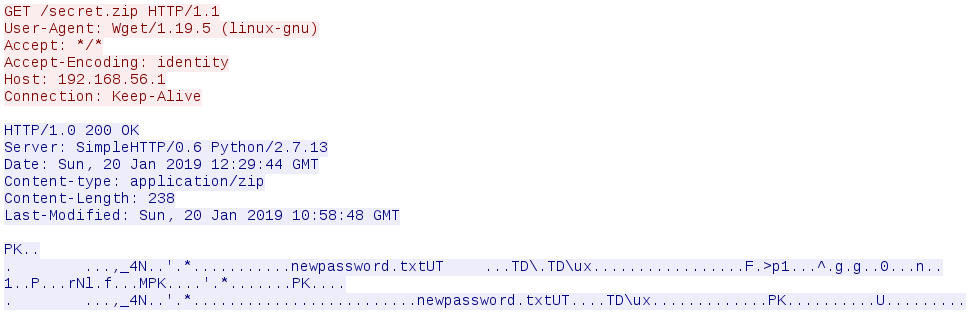
Edit > Preferences > Protocols > SSL > Pre-Master-Secret secret log filename
This secret.zip archive is protected by a simple password, so let’s try to bruteforce it with the rockyou.txt wordlist.
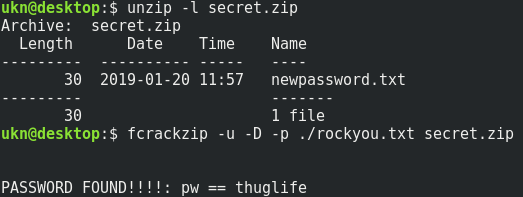
We have the password, so let’s flag now.
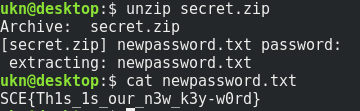
Flag : SCE{Th1s_1s_our_n3w_k3y-w0rd}
[+] Bye
Feel free to tell me what you think about this post :)