[+] Recon
This post spoils a CTF challenge … Don’t read if you want to try it !
SantHackLaus is a Jeopardy CTF challenge. It is organized by IMT Lille Douai. I had a great time solving these challenges :D
BretStiles is a forensic challenge. We need to recover the flag from a memory dump.
You can get the archive here.
We just have one file : challenge.dmp.
challenge.dmp is a Windows memory dump. Let’s analyze it with Volatility.
The best profile for this dump was : Win10x64_10586.
First, let’s enumerate the processes in this memory dump with pstree.
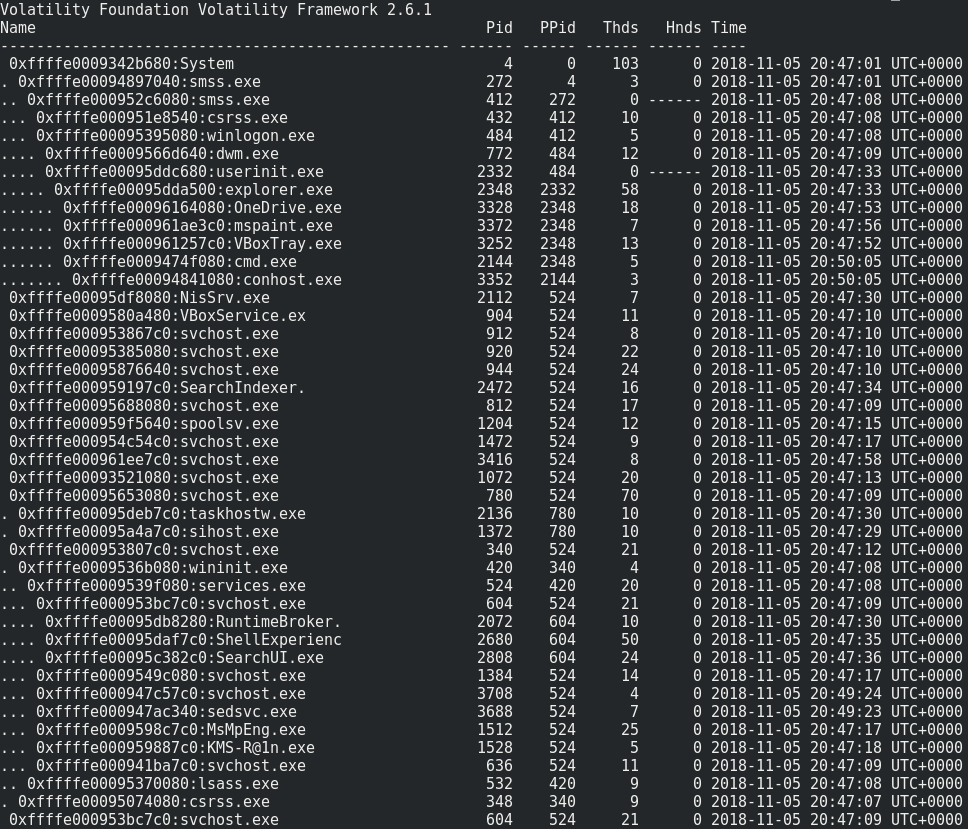
volatility -f challenge.dmp --profile=Win10x64_10586 pstree
Nothing special…
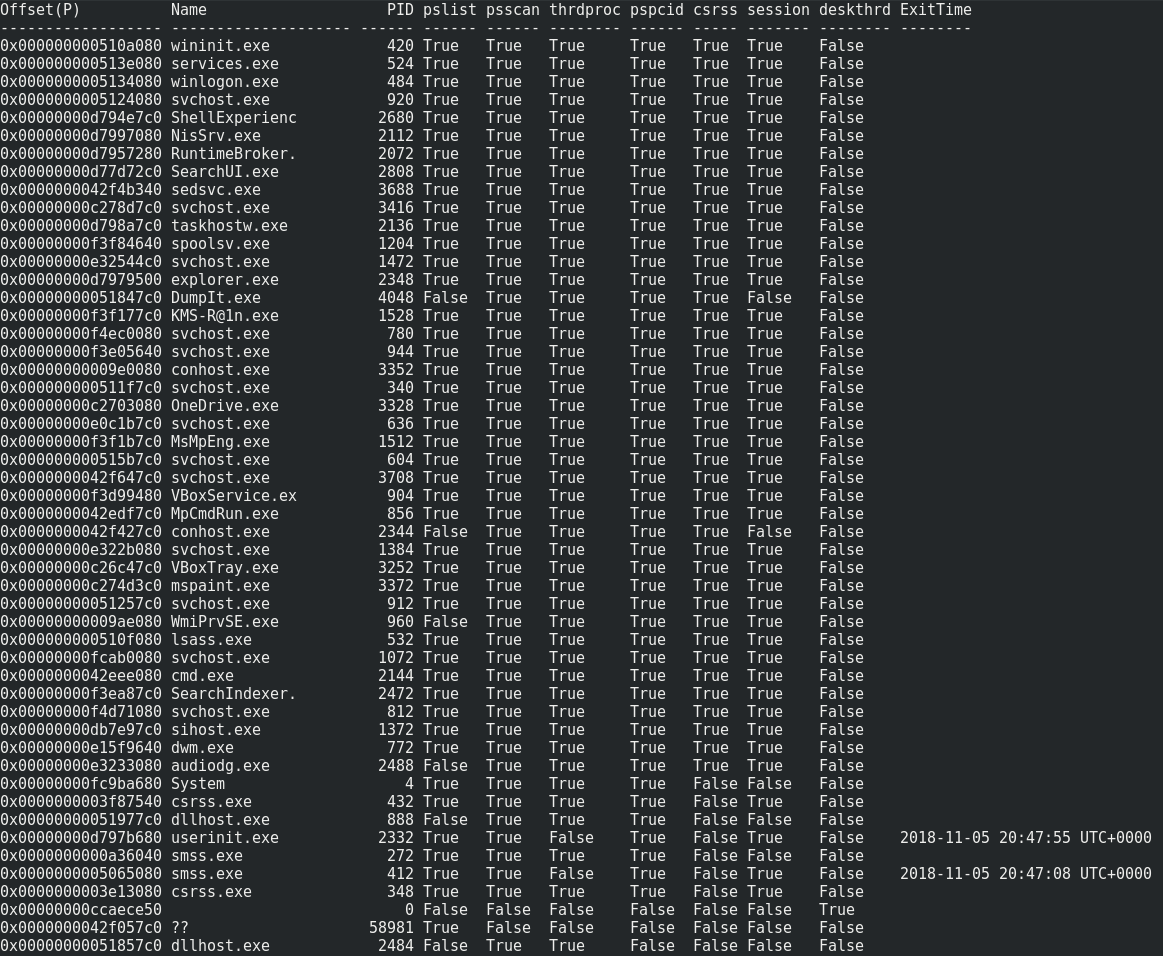
volatility -f challenge.dmp --profile=Win10x64_10586 psxview
And no hacky hidden process…
We can read the recently entered commands with “cmdline”. And there is something interesting …
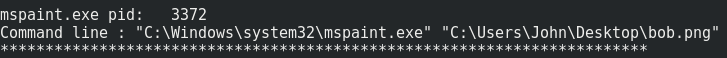
volatility -f challenge.dmp --profile=Win10x64_10586 cmdline
User ‘John’ opened the bob.png picture with paint.exe.
Let’s see if we can recover this picture from paint.exe memory. We first need to dump the process memory to a file, and then explore it with GIMP for example : volatility -f challenge.dmp --profile=Win10x64_10586 memdump -p 3372 -D ..
Finally… We found the flag at offset=320140667, width=332, height=350 in RGB Alpha mode.

Flag is : IMTLD{1m4gin4ti0N}.
[+] Bye
Feel free to tell me what you think about this post :)